Cyber Security
With cyber threats evolving faster than ever, how can your business stay secure in a landscape full of relentless risks?
Leave nothing to chance
As organisations become ever more digitally reliant, the risks to the integrity of their data also increases, resulting in many different activities and methods that seek to secure data and gain access to it.
As threats increase in their complexity and sophistication, so too does the need to pre-empt and mitigate these threats, making it hard to ensure you’ve covered all your bases. That’s where we come in.
Hear more about our unique approach to safeguarding IT environments in this short video from our security strategist, Mark Wainwright.
Cyber security without compromise
Achieve unparalleled peace of mind with comprehensive cyber security solutions designed to detect threats, enforce policies, and ensure compliance, all while providing real-time incident response and robust event logging.
Threat detection
AI-powered monitoring spots suspicious activity instantly, enabling rapid, human-led response before damage occurs.
Governance risk and compliance (GRC) services
Automated controls ensure security policies are followed consistently across your organisation.
Syscomm Secure’s built-in controls and comprehensive reporting make compliance straightforward and demonstrable.
Incident response
When threats are detected, our systems respond immediately to contain and eliminate them.
Event logging and visibility
Comprehensive audit trails track all security events, providing clear evidence for compliance and enabling continuous improvement of our protection.
Managed services
Syscomm’s managed cybersecurity services provide continuous monitoring, threat detection, and incident response to safeguard your infrastructure against cyber threats.
Pre-emptive solutions
Our expert-led approach ensures your organisation stays ahead of emerging threats with continuous security evaluation and threat intelligence.
With comprehensive assessments that include, Penetration Testing, Vulnerability Scanning, Application Testing, and Attack Surface Monitoring.
Build your digital fortress
Our distinct approach to cyber incident prevention protects your business at every level.

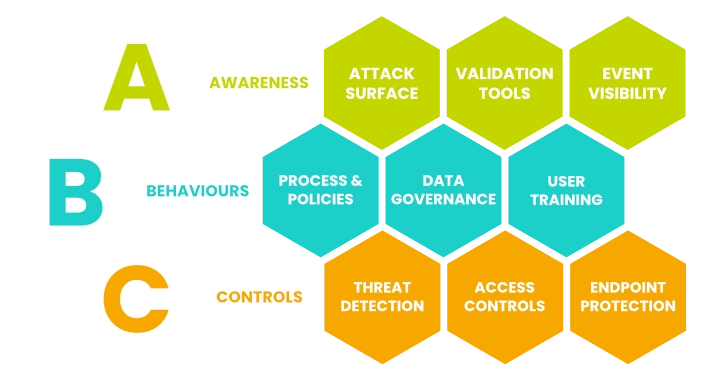
Awareness
Without knowing where the risks are, it's impossible to be effectively protected. Our Awareness services look to identify the breadth of your attack surface and where you could be open to being leveraged.
We review your existing infrastructure for known vulnerabilities, assess where you could be exploited, and provide event visibility so you can assess your security status in real time.

Behaviours
Despite having a range of security solutions in place, your users will always be the weakest link in your efforts to protect your data.
By implementing robust security policies and process, users can become more aware of their responsibility, security awareness training can empower your users to identify threats in real-time and your approach to data governance can be an effective last line of defence.

Controls
Cyber threats are happening constantly and in many different ways and so it's essential to have the right solutions in place to both detect and then respond.
As networks and infrastructures have become more sophisticated, widespread and accessible, having the right tools is critical to controlling who has access to your data.
Get IT on your side:
Book a meeting with Chris
Having helped over 200 organisations recover from security incidents, we know exactly where IT typically fails. Our assessment methodology combines this experience with advanced monitoring, providing you with:
- Improved visibility over your IT environment
- Clear understanding of how gaps affect your business
- Guidance on practical solutions that will work with your existing systems

Happy customers
Hear from clients who’ve gained total cyber security confidence after partnering with us.
“Syscomm has ensured our network and systems have continued to maintain the performance and flexibility to scale with our business advancement.”
Jason Ashby
Managing Director UKFlooring Direct
“As an IT support services company, Syscomm has proven time and again their capability and dedication across a wide range of scenarios.”
Bradley Schoenfelder
Happy Customer
“Internet connectivity is key to any school or business, and with Syscomm as an ISP, it’s a relief knowing I can sleep at night and don’t have to worry about things”
Tom Carter
Blue Coat Church of England School
Secure your entire IT ecosystem with cyber protection that delivers
When you eliminate gaps between security systems, protection becomes significantly more effective. Discover how our integrated approach makes a difference.
Total visibility
See everything that's happening in your IT environment through one unified dashboard. No blind spots, no uncertainty. Only clear, actionable intelligence about your cyber security status.
Streamlined compliance
Built-in controls and comprehensive reporting make it easier to prove your security posture to auditors and stakeholders.
Proactive prevention
Stop reacting to threats after they've caused harm. Our AI-powered monitoring spots potential issues early, enabling swift action before problems escalate.
Measurable results
Get clear metrics showing how our security measures protect your organisation. From threats blocked to response times, you'll see exactly how your investment is working.
Ready to bridge the gap between present and potential?
Gain valuable insights into your technology posture with our complimentary lite assessment.
We’ll review key areas of your IT, then highlight vulnerabilities and opportunities for improvement in an actionable report.
This snapshot will help you to see not just where your technology stands, but also how to get it out of your way and working better (and more securely) for your business.

FAQs
Find answers to your most pressing questions about our cyber security services.Have a query we haven’t covered? Get in touch!
What makes your approach different to our last IT support provider?
Unlike providers who implement disconnected security tools, we create one unified security environment.
Drawing from experience helping hundreds of organisations recover from cyber attacks, we know exactly where traditional security approaches fail – and how to prevent that from happening to you.
How does your ABC framework actually protect us?
Our approach combines advanced monitoring (Awareness) with automated policy enforcement (Behaviours) and multiple security layers (Controls). Everything works together to eliminate the gaps where threats typically hide and spread.
What happens if you detect a threat?
Our systems respond automatically to contain potential threats, while alerting our security team for immediate investigation.
We handle incidents proactively, often before they can impact your operations. It’ll be business as usual for your team, with the added confidence of expert protection.
How do you handle compliance requirements alongside cyber security?
Because data protection compliance is crucial for our clients, security compliance is built into our ABC framework.
We maintain detailed audit trails and can demonstrate compliance with major standards including GDPR, ISO27001, and more industry-specific regulations.
Can you work with our existing cyber security tools?
Yes – we can integrate existing security tools into our framework where appropriate. However, our integrated approach often means you can consolidate and simplify your security stack.
